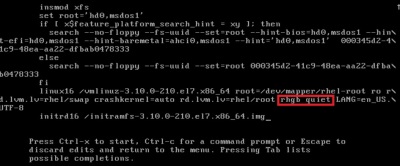
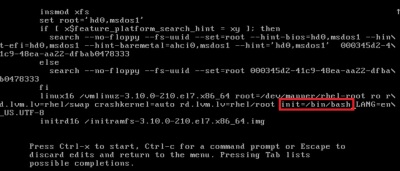
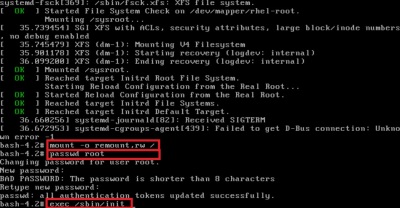
Enter into rescue mode.
mkdir /mnt/disk
mount /dev/vda1 /mnt/disk
chroot /mnt/disk –> this is to change the root.
Now vi /etc/grub.conf (if not chrooted, the file should be /mnt/disk/etc/grub.conf) and change the default value to any otehr kernel number (current kernel is 0. we have to change it to 1 or 2 or 3 like that)
# cat /etc/grub.conf
# grub.conf generated by anaconda
#
# Note that you do not have to rerun grub after making changes to this file
# NOTICE: You do not have a /boot partition. This means that
# all kernel and initrd paths are relative to /, eg.
# root (hd0,0)
# kernel /boot/vmlinuz-version ro root=/dev/vda1
# initrd /boot/initrd-[generic-]version.img
#boot=/dev/vda
default=3
timeout=5
serial –unit=0 –speed=115200
terminal –timeout=5 serial console
title CentOS (2.6.32-696.20.1.el6.x86_64)
root (hd0,0)
kernel /boot/vmlinuz-2.6.32-696.20.1.el6.x86_64 ro root=UUID=6446959f-deb2-491f-93a7-bdbbf5ebf31e consoleblank=0 crashkernel=auto SYSFONT=latarcyrheb-sun16 LANG=en_US.UTF-8 KEYTABLE=us nox2apic
title CentOS (2.6.32-696.18.7.el6.x86_64)
root (hd0,0)
kernel /boot/vmlinuz-2.6.32-696.18.7.el6.x86_64 ro root=UUID=6446959f-deb2-491f-93a7-bdbbf5ebf31e consoleblank=0 crashkernel=auto SYSFONT=latarcyrheb-sun16 LANG=en_US.UTF-8 KEYTABLE=us nox2apic
initrd /boot/initramfs-2.6.32-696.18.7.el6.x86_64.img
title CentOS (2.6.32-696.16.1.el6.x86_64)
root (hd0,0)
kernel /boot/vmlinuz-2.6.32-696.16.1.el6.x86_64 ro root=UUID=6446959f-deb2-491f-93a7-bdbbf5ebf31e consoleblank=0 crashkernel=auto SYSFONT=latarcyrheb-sun16 LANG=en_US.UTF-8 KEYTABLE=us nox2apic
initrd /boot/initramfs-2.6.32-696.16.1.el6.x86_64.img
title CentOS (2.6.32-696.10.3.el6.x86_64)
root (hd0,0)
kernel /boot/vmlinuz-2.6.32-696.10.3.el6.x86_64 ro root=UUID=6446959f-deb2-491f-93a7-bdbbf5ebf31e consoleblank=0 crashkernel=auto SYSFONT=latarcyrheb-sun16 LANG=en_US.UTF-8 KEYTABLE=us nox2apic
initrd /boot/initramfs-2.6.32-696.10.3.el6.x86_64.img
title CentOS (2.6.32-696.:wq10.1.el6.x86_64)
root (hd0,0)
kernel /boot/vmlinuz-2.6.32-696.10.1.el6.x86_64 ro root=UUID=6446959f-deb2-491f-93a7-bdbbf5ebf31e consoleblank=0 crashkernel=auto SYSFONT=latarcyrheb-sun16 LANG=en_US.UTF-8 KEYTABLE=us nox2apic
initrd /boot/initramfs-2.6.32-696.10.1.el6.x86_64.img
:wq!
Now unrescue and enter into vnc or server.
If one kernel is failed to boot, then change the kernel number until the server get booted.
Now check the old (now we have changed to current kernel) kernel
===
# uname -r
2.6.32-696.18.7.el6.x86_64
===
The kernel with issue was 20.1. The error was due to some missing modules in that kernel, due to that we got kernel panic error. So, now we have to remove that kernel without dependencies (20.1)
=====
root@162-144-43-30.webhostbox.net [~]# rpm -qa | grep 2.6.32-696.20
kernel-2.6.32-696.20.1.el6.x86_64
kernel-headers-2.6.32-696.20.1.el6.x86_64
kernel-devel-2.6.32-696.20.1.el6.x86_64
kernel-firmware-2.6.32-696.20.1.el6.noarch
root@162-144-43-30.webhostbox.net [~]# rpm -e –nodeps kernel-2.6.32-696.20.1*
warning: erase unlink of /lib/modules/2.6.32-696.20.1.el6.x86_64/modules.order failed: No such file or directory
warning: erase unlink of /lib/modules/2.6.32-696.20.1.el6.x86_64/modules.networking failed: No such file or directory
warning: erase unlink of /lib/modules/2.6.32-696.20.1.el6.x86_64/modules.modesetting failed: No such file or directory
warning: erase unlink of /lib/modules/2.6.32-696.20.1.el6.x86_64/modules.drm failed: No such file or directory
warning: erase unlink of /lib/modules/2.6.32-696.20.1.el6.x86_64/modules.block failed: No such file or directory
====
Now update the kernel.Our current kernel is 18.7 and it will update to 20.1
===
root@162-144-43-30.webhostbox.net [~]# uname -r
2.6.32-696.18.7.el6.x86_64
===
Now shut down
===
[~]# shutdown -r now
Broadcast message from root@162-144-43-30.webhostbox.net
(/dev/pts/0) at 8:26 …
The system is going down for reboot NOW!
===
Now check and the kernel should be 20.1
===
# uname -r
2.6.32-696.20.1.el6.x86_64
===
Now check grub.conf
======
default=0
timeout=5
serial –unit=0 –speed=115200
terminal –timeout=5 serial console
title CentOS (2.6.32-696.20.1.el6.x86_64)
root (hd0,0)
kernel /boot/vmlinuz-2.6.32-696.20.1.el6.x86_64 ro root=UUID=6446959f-deb2-491f-93a7-bdbbf5ebf31e consoleblank=0 crashkernel=auto SYSFONT=latarcyrheb-sun16 LANG=en_US.UTF-8 KEYTABLE=us nox2apic
initrd /boot/initramfs-2.6.32-696.20.1.el6.x86_64.img
title CentOS (2.6.32-696.18.7.el6.x86_64)
root (hd0,0)
kernel /boot/vmlinuz-2.6.32-696.18.7.el6.x86_64 ro root=UUID=6446959f-deb2-491f-93a7-bdbbf5ebf31e consoleblank=0 crashkernel=auto SYSFONT=latarcyrheb-sun16 LANG=en_US.UTF-8 KEYTABLE=us nox2apic
initrd /boot/initramfs-2.6.32-696.18.7.el6.x86_64.img
title CentOS (2.6.32-696.16.1.el6.x86_64)
root (hd0,0)
kernel /boot/vmlinuz-2.6.32-696.16.1.el6.x86_64 ro root=UUID=6446959f-deb2-491f-93a7-bdbbf5ebf31e consoleblank=0 crashkernel=auto SYSFONT=latarcyrheb-sun16 LANG=en_US.UTF-8 KEYTABLE=us nox2apic
initrd /boot/initramfs-2.6.32-696.16.1.el6.x86_64.img
title CentOS (2.6.32-696.10.3.el6.x86_64)
root (hd0,0)
kernel /boot/vmlinuz-2.6.32-696.10.3.el6.x86_64 ro root=UUID=6446959f-deb2-491f-93a7-bdbbf5ebf31e consoleblank=0 crashkernel=auto SYSFONT=latarcyrheb-sun16 LANG=en_US.UTF-8 KEYTABLE=us nox2apic
initrd /boot/initramfs-2.6.32-696.10.3.el6.x86_64.img
title CentOS (2.6.32-696.10.1.el6.x86_64)
root (hd0,0)
kernel /boot/vmlinuz-2.6.32-696.10.1.el6.x86_64 ro root=UUID=6446959f-deb2-491f-93a7-bdbbf5ebf31e consoleblank=0 crashkernel=auto SYSFONT=latarcyrheb-sun16 LANG=en_US.UTF-8 KEYTABLE=us nox2apic
initrd /boot/initramfs-2.6.32-696.10.1.el6.x86_64.img
~
====
That’s it.